Reverse Engineering with Ghidra
- ISSP
- Apr 23, 2019
- 6 min read
Updated: Oct 18, 2022
Ghidra is a tool for reverse engineering, which has been used for many years by special services. Now it is available to everyone. In this article you will find a step-by-step guide.
Meet the Ghidra. Introduction
Not long ago the US National Security Agency released a reverse engineering tool called Ghidra. Information about this tool was already known from the “Vault 7” series by WikiLeaks as of March 2017, where a number of hacking tools used by the CIA were discussed and Ghidra was repeatedly mentioned as a reverse engineering tool created by the NSA. However, until recently its source code was unavailable.
Ghidra runs on Windows, macOS and Linux and has all the components that security analysts expect from it. It is comparable to IDA, Radare2 and Binary Ninja, which we are so familiar with. The tool enables flexible configuration and is designed to facilitate multi-user work on the same reverse project. In this article, we will look at Ghidra features by analyzing a simple crackme.
Basic Information About the Ghidra
Installation of Ghidra
First, the successful startup of Ghidra requires the installation of some additional software. Ghidra requires JDK 11, so download the installer from here (https://www.oracle.com/technetwork/java/javase/downloads/jdk11-downloads-5066655.html) and run it. As soon as this has been done, get the latest Ghidra version from the official website (https://www.ghidra-sre.org). When the installation is completed unpack the file and double click “runGhidra.bat” to run Ghidra. On initial start-up, user agreement will be displayed, and after a short installation, you will see the project’s pop-up window. If you experience any installation problems or problems with the instructions above, please read the guide by clicking the following link: https://www.ghidra-sre.org/InstallationGuide.html#Install.
Project Creation
Project window enables downloading and managing binary files. The crackme0x00.exe binary file which we are going to work with is available for downloading here (https://github.com/Maijin/Workshop2015/tree/master/IOLI-crackme/bin-win32). Create a new project and import the downloaded crackme0x00.exe file. This can be done by dragging and dropping the binary file into the project window or by selecting File -> Import File in the project window options. After this has been done you will see the downloaded crackme0x00.exe file.



Next, double click crackme0x00.exe in the project window to open the code browser. A message box with the question “Do you want to analyze the binary file?” will be displayed. Select “Yes” and you will be shown various types of analysis available. Default settings are suitable for this project, so select “Analyze” and wait until Ghidra has completed the task. As soon as this has been done, the code browser and main windows will be displayed.

Main Windows
Let’s look at the main windows Ghidra has in Code Browser. One interesting thing Ghidra offers is context help. For most interface elements you may press F1 when mousing over to open help information on what you want to learn more about.
With the help of the “Program Trees” window, you may right-click the crackme0x00.exe folder to manage reverse engineering code sections in a different way. You may do it by selecting “Modularize By” and then “Subroutine”, “Complexity depth” or “Dominance”. You may also create new folders and drag and drop sections according to your own managing preferences.

The next window under “Program Trees” is “Symbol Tree” which enables viewing import, export, functions, labels, classes and namespaces of a binary file. Try expanding the “Import” section to see various DLL libraries and their functions. If you want to see where specific functions are displayed in a binary file, you may right-click the function and select “Show References to”, and then double-click the results to see the full section.

“Data Type Manager” allows you to see all specific types, including built-in ones, specific for the binary file and other types included Ghidra (for example, those we see in Windows called “windows_vs12_32”). Try unpacking the book icons and right-clicking on Data Type. Then click “Find Uses of” to see where this data type is used in the binary file.

Now we find ourselves in one of the key “attractions”, the “Listing” window. Here you can see the reverse-engineered code. Ghidra offers you numerous ways of configuring the listbox. To do this, you may click on the icon “Edit the listing fields” in the top right corner and then click the “Instruction/Data” tab. Any element of the listing interface may be changed, relocated, disabled or removed. You may also add new elements by right-clicking and using the context menu. Try changing the “Address” field size by reducing it, and remove the “Bytes” field.

You will see the context menu in the reverse engineering listing by right-clicking somewhere in the assembly code. You may correct instructions, set bookmarks, comment and edit shortcuts. Try right-clicking one of the instructions and adding a comment. You may double-click one of the functions referenced in “CALL” to go to the function code and get a better idea of what it can do. Navigate by clicking the arrows in the top left corner, using the “Save” icon or “Alt-Left Arrow Key” and “Alt-Right Arrow Key” key combinations.

Those familiar with IDA Pro are used to working in “Main” and “Graphic” modes. Ghidra has a similar window called “Function Graph”, which can be accessed by clicking “Window” and “Function Graph”. Function graph may also be set using the “Edit the listing fields” button. Graphs in Ghidra by default do not display a comment field so try adding them with the help of Field Editor.

Finally, we will see the “Decompile” window on the right which shows a high-level code generated by Ghidra representing an assembler code in the “Listing” window. Try highlighting one of if-operators in Decompiler and you will notice that it highlights the relevant assembly. This is one of Ghidra’s features that’s really convenient as it enables you to get an idea of which groups of assembler instructions match which high-level instructions.

You may right-click on variables to rename them or add comments in Decompiler. They will also be displayed in the “Listing” window. Ghidra synchronizes all those windows automatically. If you wish to set any of the decompiler display parameters, you may do it by right-clicking in the window and selecting “Properties”. See if you may rename local variables to something more self-explanatory and note that your changes appear in the “Listing” window as well.
Applying the knowledge gained when studying CrackMe
If you’ve made it so far, you must understand Ghidra’s key interfaces and be ready to cope with the first CrackMe. Start with running the crackme0x0.exe file to see how the program works. You will notice that it requests a password, assesses the data entered by a user and responds with the “Invalid Password!” message where the data entered were incorrect.

Let’s perform initial sorting of this binary file by viewing program strings in the “Window -> Defined Strings” window. You will see part of the text displayed in the command line. Let’s discuss the part of assembly that refers to “Password”. Double-click the “Password” entry in the “Defined Strings” window and you will be taken to the section where the text is stored in the program.

Left-click the address and select “References -> Show References to Address”. You may click on the entry to go to the code section with “Password” reference. Alternatively, you may double-click on the address located to the top right of the line with an XREF[1] note. Try finding out which assembly section is responsible for matching user inputs and correct password. Rename the variables and functions to something more descriptive.
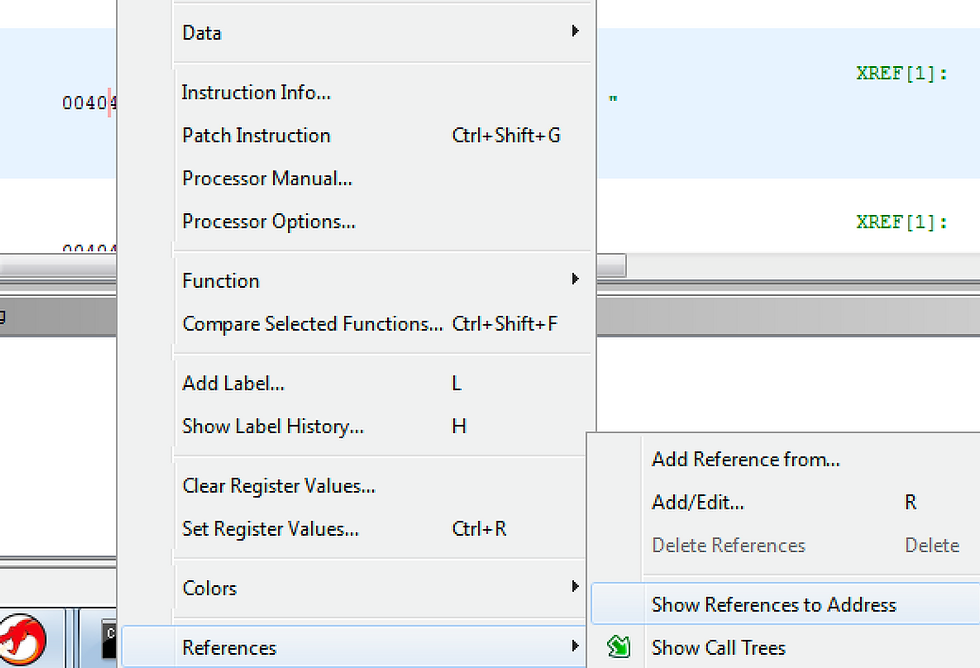

You will notice that after the reference to “Password” there is a scanf call for obtaining user input and then a strcmp call. We can see that user input is saved in EAX and put into the local variable “local_40”. The “250382” line is also saved in the local variable “local_3c” and then both are moved to strcmp. The result of this matching is compared to zero, and if it equals zero, “Password OK :)” text is typed. Otherwise, it switches and types “Invalid Password!” text.

Let’s run “crackme0x00.exe” again, assign it the password “250382”. The following must be displayed:

Conclusions
As a result of this article, not only have we got ourselves familiar with the Ghidra tool, but also taken the first steps towards reverse engineering and cracking. Ghidra resources do not end here. Nor does its potential for use. Despite the fact that no backdoors included by the NSA in the tool have been found, analysts warn about vulnerability of executing the remote code. That’s why we are exploring new reverse engineering platforms and staying alert. Hopefully, taming the dragon called Ghidra will be as easy for you as it was for Jon Snow from the Game of Thrones:) See you next time in our more advanced lessons on how to use Ghidra in our difficult job of reverse engineering.
To learn more about ISSP Professional Services visit ISSP Labs and resource center
Where should be placed the FIDB files in Ghidra directory? (path)
`ecos-mips.be.32.fidb` and `ecos-mips.le.32.fidb`